As software solutions are getting more sophisticated and business agility is becoming more crucial day by day, more and
more companies look towards the implementation of DevOps or DevSecOps. These are real buzzwords today. But it is no
wonder with regard to what these two software development methodologies promise - high team productivity and super fast
delivery of new features and updates, and all of these without compromising on product quality and security. Sounds
great, doesn’t it?
If you are one of those who would like to adopt DevOps or DevSecOPs, yet you are not sure which one to choose, you are
in the right place. We are going to discuss the fundamental difference between DevOps and DevSecOps along with the
advantages and peculiarities of each approach.
Understanding DevOps
As you might know, the traditional approach to software development suggests a clear division of responsibilities and
therefore the isolated work of each team. A development team creates a product, then a QA team checks it, and finally
after bug-fixing an operation team deploys and maintains the product.
It was a usual practice for many years, however, some people within the IT community concluded that this approach is far
from being productive and that instead of a few separated teams, there should be one cross-functional team containing
both developers and operations specialists.
The official inception of DevOps is related to the presentation of Patrick Debois in 2009, where he presented the term
DevOps and the key concept behind it – efficient collaboration of developers and ops specialists.
So DevOps is a modern approach to software development that speeds up software development and deployment as well as
increases their efficiency by means of the automation of related tasks and the collaboration of software engineers and
ops experts realized through a culture of close communication and joint responsibility. So cooperation and automation
are the twin pillars on which this methodology is built.
As to the collaboration, everything is clear. By nurturing shared accountability, open communication, shared goals,
ongoing feedback, and knowledge sharing, DevOps teams become more productive and enhance the quality of their work.
Automation, in turn, is a real driving force that enables software delivery at a really high speed. So DevOps implies
the automation of different processes and the heavy use of various automation tools.
With regard to everything mentioned above, a shift to DevOps requires particular hard skills as well as a significant
change in team culture and mindset.
To clearly understand the concept of DevOps, it is also worth getting acquainted with its key practices. Here are some
of them:
The first thing that comes to mind when someone mentions DevOps is definitely a CI/CD pipeline. Indeed, this is a
paramount practice of DevOps. CI/CD stands for Continuous Integration and Continuous Delivery or Continuous Deployment.
In essence, it is a combination of several practices employed to automate and optimize coding, building, testing,
packaging, and deploying. In such a way faster development cycles, better code quality, and higher team productivity are
provided.
Due to the fact that CI/CD lies at the heart of DevOps, we cannot help but review each of its constituent components.
Continuous Integration: As a rule, a team integrates code changes into a shared repository many times per day. Automated
tests ensure that the newly integrated code does not introduce any errors or conflicts with existing code. The key goal
of CI is to catch and eliminate integration bugs, optimizing the maintenance of code quality and stability.
Continuous Delivery: CD extends CI by automatically deploying code changes to a staging or pre-production environment
where they are further meticulously tested. The code is constantly kept in a deployable state to ensure manual testing
and any other QA processes. The mission of CD is to assure code readiness for production. Still, human intervention is
required to trigger the final deployment to a live production environment.
Continuous Deployment: It takes a step further by automatically deploying all code changes to the live production
environment once they pass all tests and validations. In such a way Continuous Deployment makes manual intervention
unnecessary in the deployment process and ensures rapid delivery of new features and improvements to end users.
IaC or infrastructure as a code is one more fundamental practice of DevOps. It can be defined as a special strategy for
the management and provision of infrastructure resources that suggests using scripts and automation instead of manual
task handling or traditional configuration management tools.
Using IaC, one can define and describe the needed state of infrastructure with the help of code, which is then executed
to automatically set a deployment environment (networks, databases, virtual machines, etc.) with the needed
configurations.
With an environment configured as code, a team can test it the same way as it tests source code. A virtual machine that
behaves like a production environment can be leveraged to test early. Whenever there is a need for scaling, the code can
automatically set the needed number of environments that are consistent with each other.
To wrap it up we would like to say that this is actually IaC that makes continuous delivery possible.
Containerization is a practice that implies packaging applications and their dependencies into lightweight and
standardized container images. These containers involve everything needed to run an application, including code, runtime
components, libs, and system tools.
Containerization provides a consistent and isolated environment that can be easily deployed across environments of all
types. This practice is well combined with the IaC described above.
Containerization perfectly supplies the DevOps needs because it enables the work of CI/CD pipelines. Teams package their
apps into containers, test them, and then deploy these containers.
Microservices is a popular approach to software architecture according to which an application is built as a set of
rather small, hardly coupled, and separately deployable services. Each service is responsible for a particular business
functionality and interacts with other services via application programmer interfaces. When integrated with DevOps
practices, microservices offer numerous benefits. Thus it enables frequent releases and faster delivery of new features
and updates. Microservices also provide isolation that simplifies debugging and troubleshooting. Individual
microservices can be scaled depending on current demand, which optimizes resource usage and improves app performance. A
different technology stack can be leveraged for each service, promoting innovation and flexibility. These are just a few
benefits to mention.
DevOps is also not possible without continuous monitoring, which involves ongoing, automated collection and analysis of
data about the app's performance, security, and overall health. In essence, it provides insights into the state of
software and infrastructure, enabling DevOps teams to catch issues, recognize trends, and make informed decisions to
streamline a software delivery process. Ongoing monitoring comes with numerous advantages including real-time
visibility, early error detection, performance optimization, automated alerts, fast incident response, and a short
feedback loop.
To wrap it up we would like to point out that DevOps is an efficient modern approach that automates and streamlines
numerous aspects of software development so that teams can deliver new anxiously awaited features within the shortest
possible time.
Introducing DevSecOps
Now let’s shift our attention to DevSecOps. In a nutshell, it can be defined as an upgraded version of DevOps that is
laser-focused on ensuring solid software security and complete regulatory compliance.
With the number of threats constantly growing and cybercriminals becoming more inventive, many businesses have concerns
about the necessity to ensure rocket-solid data protection. Besides, strict state regulations and different security
standards also encourage companies to prioritize security in the development of their software solutions. All of these
have given rise to DevSecOps or Development, Security, and Operations.
DevSecOps is a special software development strategy that lays solid stress on the integration of various security
practices into all stages of the DevOps lifecycle. DevSecOps provides proactive and mainly automated security measures
to recognize and fix security weaknesses and threats as early as possible.
According to DevSecOps, not only do security experts ensure a high security level but also the rest team members –
software engineers and ops specialists – take care of it and perform their tasks with security considerations in mind.
Do you remember what we said about DevOps above? Well, all of these are valid for DevSecOps too. Still, with regard to
the fact that the latter is focussed on security, we would like to highlight some of its key principles. Here we go.
This is a basic concept of DevSecOps, according to which security considerations are moved earlier in the SDLC. Thus,
security is not treated as a post-development concern anymore but is addressed from the off – at the design and coding
stages. By applying the shift left concept to security, teams can identify security flaws early, eliminate them
immediately, and facilitate rapid, seamless delivery cycles.
We have mentioned that automation lies at the heart of DevOps. Well, it also plays an important role in DevSecOps. The
vast majority of security and compliance checks are automated and smoothly integrated into a CI/CD pipeline. Automation
enables short feedback, fast response, and immediate elimination of security issues.
DevSecOps suggests executing ongoing security testing, including SAST, DAST, IAST, security scanning of containers, etc.
Being executed on an ongoing basis these tests help uncover security weaknesses and flaws in both app code and
infrastructure.
In DevSecOps teams developers should write code in alignment with the latest coding practices. This way the code is less
exposed to well-known security vulnerabilities, including cross-site scripting (XSS), SQL injections, and buffer
overflows.
This is a suite of essential activities in DevSecOps that proactively identify, assess, and fix security weaknesses and
flaws throughout the SDLC. All software engineers, architects, and designers should strive to include threat modeling in
their work. Optimally, it is advised to create threat models at the initial stage of software development. As a rule,
this practice suggests studying data flows in an app to understand where it might be attacked, identifying as many
potential hazards as possible, and coming up with security controls that should be introduced to diminish the likelihood
or impact of potential threats.
Among others, DevSecOps also implies automation and integration of compliance checks into a CI/CD pipeline. This way one
can be confident that software and infrastructure meet corresponding compliance and security requirements. This allows
businesses to avoid possible legal issues and heavy penalties.
DevSecOps teams design incident response plans and introduce corresponding processes to swiftly handle security
incidents and data breaches. It also includes tracking, detection of abnormal behavior, and immediate response to any
alert.
Continuous monitoring, short feedback, and ongoing improvement are paramount to DevSecOps. DevSecOps teams regularly
assess their security strategy, check the effectiveness of taken security measures, and tweak them accordingly.
All specialists engaged in the process of software delivery must be familiar with basic security principles, including
OWASP. Developers, QA engineers, ops specialists, and security experts should cooperate closely and keep each other
updated on the security policies of a company. All of them should undergo periodic training to ensure they are well
aware of the latest security trends and practices.
DevSecOps advocates close cooperation and communication between developers, ops experts, and security specialists. A
DevSecOps team is collectively accountable for ensuring the security of each component and configuration. Everyone on a
product team contributes to the detection and mitigation of security threats.
To sum it up we would like to say that DevSecOps employs the DevOps lifecycle as a basis and seasons it well with
security practices to ensure solid security of applications and infrastructure.
Differences between DevOps and DevSecOps
With regard to the fact that DevSecOps has derived from DevOps, we can say that both approaches have much in common. So
what is the difference between DevOps and DevSecOps? The primary difference between them is the way they treat security.
In comparison with DevOps, security is a foundational aspect of DevSecOps. Consequently, we can notice certain
discrepancies between them.
Developers and ops specialists work as one tight-knit to increase productivity while the efficiency and high speed of software development and delivery are their common obligations.
Developers, security experts, and ops specialists combine their efforts to ensure solid security which is their common obligation.
To fill the communication gap and facilitate software development and deployment.
To ensure the decent security of software and infrastructure.
DevOps puts stress on efficiency, velocity, and quality.
DevSecOps prioritizes security and regulatory compliance.
Security is deemed to be the accountability of a security team only. Security tests are executed at a particular point of time, usually at the close of the SDLC.
Security is a shared accountability of all teams. Security tests, checks, and audits are carried out throughout the whole SDLC.
Software engineers and ops specialists work all together.
Software engineers, ops specialists, and security professionals work all together.
Teams implement key DevOps practices and set up a CI/CD pipeline.
Teams implement key DevOps practices, set up a CI/CD pipeline, and introduce a wide range of security-related processes.
Since DevOps has a goal to provide frequent releases and updates, its software development cycles are short.
Compared to the traditional approach, DevSecOps offers much shorter development cycles. Still, in comparison with DevOps, it requires more time because of the implementation of diverse security practices and the execution of numerous security checks.
So as you might notice, DevSecOps prioritizes security above all. It uses all DevOps practices and complements them with
security measures, which makes DevSecOps more comprehensive compared to DevOps.
Being primarily concentrated on velocity and engaging security professionals only at the end of software development,
DevOps may overlook some security risks and flaws. DevSecOps, in turn, treats every stage of software development with
regard to security requirements and possible risks. Applying security by design rather than tacked-on security,
DevSecOps prevents numerous security problems or nips them in the bud. If data safety is of utter importance for your
project, DevSecOps is definitely the way to go.
DevOps Approach
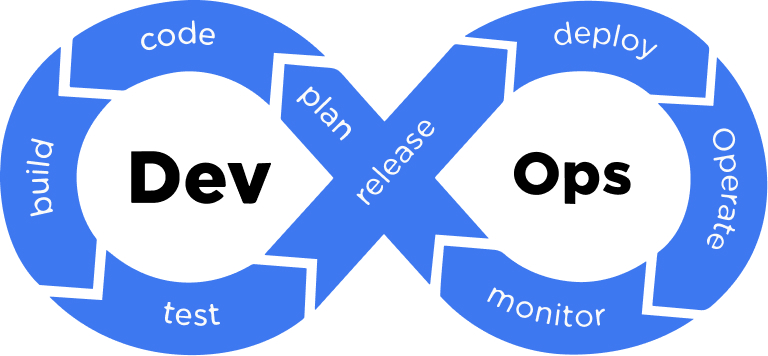
The DevOps lifecycle is an ongoing and iterative process of software development. It places a lot of emphasis on
cooperation and communication between developers and ops experts to deliver software products more efficiently and with
better quality. In general, the DevOps lifecycle includes the following stages:
Plan
In this stage, developers, and ops specialists combine their efforts to plan the next iteration. They define goals, work
scope, requirements, infrastructure needs, timelines, and resource allocation. User story creation and acceptance
criterion definition are among the key activities as well.
Code
Developers start writing code being guided by the requirements and user stories defined in the previous phase. A version
control tool, for example, Git, is used to track change history. The written code is frequently integrated into a shared
repository.
Build
CI processes are applied to automatically build and compile the code once changes have been committed to the repository.
Unit tests along with automated code quality checks are run in the course of the build stage to detect possible issues
earlier.
Test
Automated testing is a paramount part of DevOps. Tests of various types are carried out to ensure code quality and
functionality. Test environments mimicking the production ones ensure more accurate testing results.
Package
The app and its dependencies are packaged into deployable artifacts, such as containers, virtual machine images, or
application packages. All these artifacts are versioned and tagged to ensure easy change tracking and reproducibility.
Deploy
Deployment to any environment is automated to provide consistency and prevent human errors. This is realized with the
help of different tools including Jenkins or GitLab CI/CD. The IaC principles are introduced to automate the supply and
configuration of various infrastructure components. Configuration files determine the needed state of infrastructure,
and modifications are made programmatically. Terraform or AWS CloudFormation are tools that are usually utilized for
this purpose.
Monitor
Continuous monitoring solutions are leveraged in this stage to collect data about app and infrastructure performance.
Diverse logs, metrics, and events are gathered and analyzed in real time. It helps uncover errors, track performance,
and ensure app availability.
Feedback and Improvement:
Feedback loops are established to gain insights from monitoring and get user feedback. This information is valuable as
it helps to identify areas for further improvement, prioritize new features, and iterate on the development process,
launching the cycle again.
The DevOps lifecycle is characterized by extensive automation, close cooperation, and stress on continuous improvement.
Being implemented properly, DevOps helps to speed up development, improve release frequency, and enhance software
quality.
DevSecOps Approach
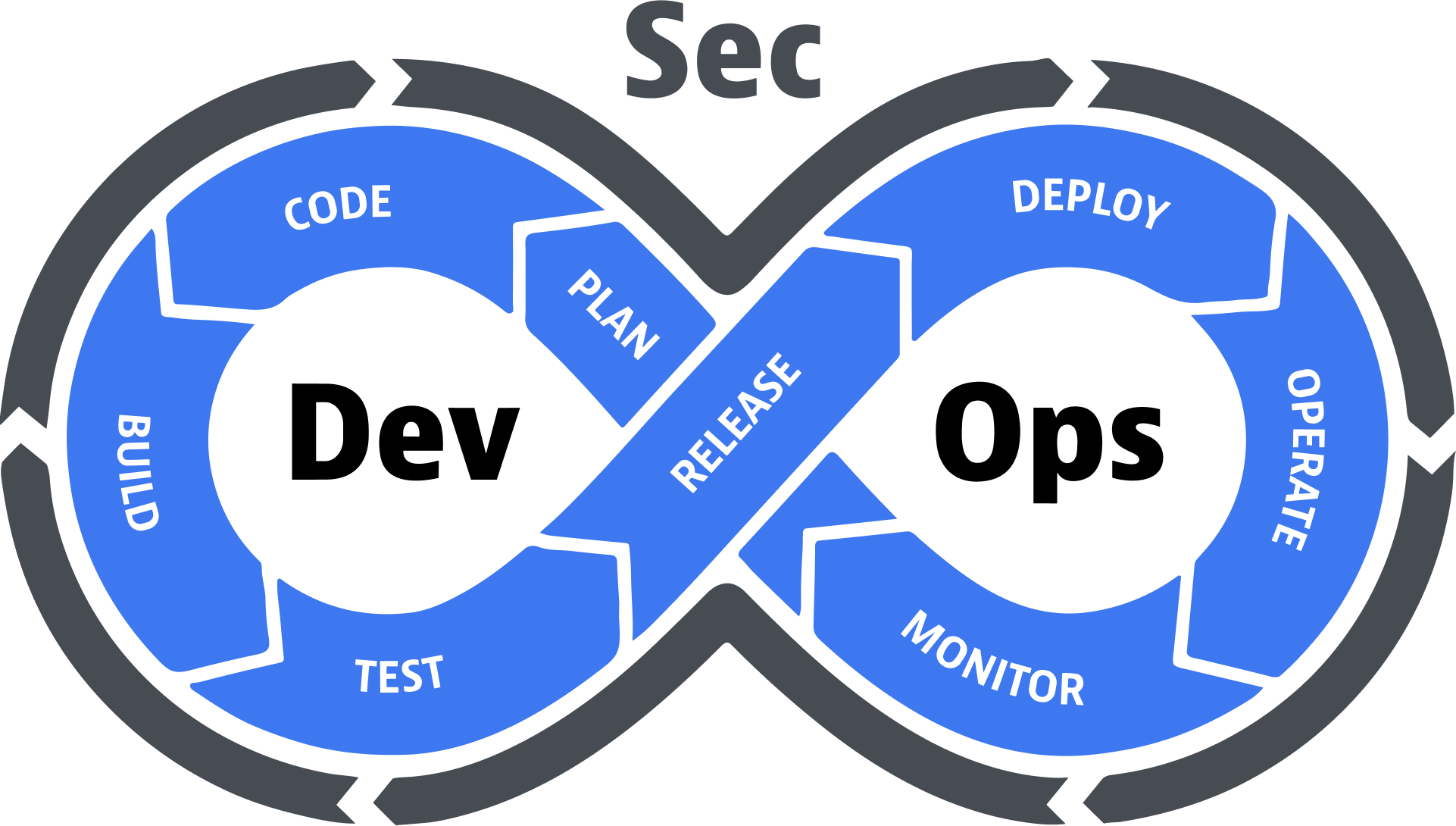
As we know, DevSecOps strives to bring security practices into each and every stage of the DevOps lifecycle ensuring
that possible security problems are handled early and consistently. That is how it works:
Plan
In this stage, teams identify security requirements and applicable compliance regulations. Threat Modeling is performed
to define possible security risks, hazards, and loopholes in the app architecture. This DevSecOps stage is marked by
cooperation, communication, review, and design of the security strategy.
Code
Developers write code following secure coding practices to guarantee resistance to SQL injections, cross-site
scripting (XSS), and other common security threats. Code reviews, along with pre-commit hooks, are usual practices for
this DevSecOps stage as well. Additionally, the code can be checked for security issues with automated static code
analysis tools like Gerrit, SpotBugs, Phabricator, PMD, and CheckStyle.
Build
At this stage, a build output artifact is automatically checked for security. It is critical as developers far too often
rely on different external, sometimes completely unreliable dependencies that can accidentally or intentionally contain
exposures. Pivotal security practices in this stage are software component analysis, unit testing, and SAST, which are
also automated and integrated into a CI/CD pipeline. SonarQube, OWASP Dependency-Check, Snyk, SourceClear, and Checkmarx
are tools that are usually utilized for the build stage analysis.
Test
An extensive set of tests should be executed in this stage. In terms of security, DAST tools are leveraged to check user
authentication, authorization, SQL injection, and API endpoints. The market offers a lot of free and commercial security
testing tools with rich functionality and multiple language support. OWASP ZAP, JBroFuzz, IBM AppScan, Boofuzz, and
GAUNTLT are just a few of them that you can use in this stage.
Package
In the packaging stage containers, virtual machine images, or application packages undergo security scanning to make
sure that they do not contain any known threats. To prevent tampering and corruption, digital signatures can be used to
verify the authenticity and integrity of code and artifacts.
Deploy
By this stage, the app code should already be meticulously tested. Therefore, the main focus here is on the verification
of a runtime environment infrastructure. Configuration management tools – Puppet, Ansible, Chef, HashiCorp Terraform,
and Docker – play an essential role in this stage because they help to get visibility into the static configuration of a
dynamic infrastructure.
Monitor
Continuous monitoring is implemented to detect suspicious activities, abnormalities, unauthorized access, etc. Security
information and event management tools like Datadog, Logpoint, Graylog, SolarWinds, and others are usually employed for
this purpose. They collect event log information from diverse sources, use real-time analysis to detect activities
deviating from the norm and take needed measures. This way teams get visibility into activity within their network to be
able to respond properly and quickly to potential cyberattacks and align with compliance requirements.
Feedback and Improvement
A team uses insights gained from continuous monitoring and incident response to improve security strategy. Moreover, to
reinforce security consistently and continuously, the team frequently takes security training courses and participates
in security awareness programs to introduce brand-new security practices and update existing ones.
The DevSecOps lifecycle encourages a culture of shared accountability for security and bakes security practices into all
its stages. This way organizations can proactively address security issues, which lets them deliver more dependable and
resilient applications.
Benefits: DevOps vs. DevSecOps
Either DevOps or DevSecOps can bring businesses a bunch of benefits. Again, discussing this topic we should remember
that DevSecOps is based on DevOps. With regard to this, we would like to start with the advantages of the latter as they
work for the former too. Then, we will review the advantages of DevSecOps in particular.
DevOps Benefits:
DevOps immensely streamlines a software delivery pipeline by automating numerous related processes. It gives an
opportunity to release new features or updates very quickly.
Due to an iterative approach and optimized processes, DevOps allows businesses to quickly adapt and respond to
ever-changing market needs. Obviously, such business agility helps to stay ahead in the market and obtain the
scalability required to transform the business.
DevOps fosters close and open communication between software engineers and ops specialists, which ensures better
coordination and problem-solving.
Since most processes within DevOps are automated, a team has more time to frame new ideas and drive innovation.
Automation of numerous processes prevents human errors while holistic testing and ongoing monitoring realized within the
DevOps lifecycle help to catch bugs early and fast. In such a way DevOps teams deliver software of excellent quality.
DevOps leverages automated recovery and failover mechanisms that make software even more resilient to disruptions,
reduce downtime, and enhance user experience.
High product quality, quick delivery of new features, fast bug fixing, and speedy response to user feedback help to
ensure a high user satisfaction rate. All of these also lead to high user acquisition and retention rates.
DevSecOps Benefits:
DevSecOps considers security aspects at the outset of software development and then infuses security practices at each
stage. Therefore, code passes consistent reviews, audits, tests, and scans throughout the development process. This way
security issues can be addressed before they cause more dependencies. In such a way security becomes more effective and
less expensive.
DevSecOps integrates automated security testing, vulnerability detection, and patching into a CI/CD pipeline to avert
the release of insecure software. Early patching does not let cybercriminals exploit vulnerabilities.
Along with security tests, DevSecOps integrates automated compliance checks across various stages of software
development, enabling complete alignment with corresponding regulatory requirements like HIPAA, PIPETA, GDPR, etc.
When a team detects and handles security issues continuously, it prevents the accumulation of security debt and
eliminates the need for extensive security patches later.
DevSecOps suggests designing an efficient incident response plan, thanks to which teams can quickly and properly respond
to security incidents.
In summary, both DevOps and DevSecOps provide numerous advantages including high productivity, business agility,
excellent quality, and resilience. Yet, DevSecOps goes further by implanting security into all processes, which results
in decreased software exposure to security threats.
Challenges and Considerations
As to the difficulties associated with the adoption of DevOps and DevSecOps, they are actually the same. It is necessary
to properly handle them to implement these approaches properly and yield benefits from them. So let's review common
challenges and potential solutions for both DevOps and DevSecOps:
Do not be surprised to find your teams reluctant to change their usual routine practices to new ones. It is always
difficult to step out of your comfort zone.
Solution for DevOps: Encourage a cultural shift by fostering close cooperation and communication between software
engineers and ops specialists. Promote shared responsibility for development deliverables.
Solution for DevSecOps: Push the idea about the necessity to cooperate with a security team. Highlight the utter
significance of security and the efficiency of shared accountability for it.
If you have decided to switch from the traditional approach to DevSecOps or DevOps, there can be a considerable
knowledge gap related to a lack of expertise in automation tools, unfamiliarity with DevOps/DevSecOps principles, vague
understanding of modern infrastructure concepts, and ignorance of security practices.
Solution for DevOps: To overcome this challenge, invest in DevOps practice training programs and workshops to let team
members enrich their skills and knowledge, promote knowledge sharing, ongoing education, and continuous improvement, and
develop comprehensive documentation and knowledge repositories that capture best practices and procedures. It may help
to bring in external DevOps consultants who can provide you with guidance.
Solution for DevSecOps: Provide security courses and awareness programs for all team members, ensuring that they
clearly understand security practices and their importance. Develop and maintain comprehensive security documentation
and secure coding guidelines tailored to the specific DevSecOps processes within your company. Make these resources
readily accessible to all your team members. Engagement of external security consultants so that they can offer insights
and best practices using their extensive security expertise can be a way to go as well.
Software teams use various types of tools to develop applications, deploy them, and test their security. Integration of
tools from diverse vendors into one CI/CD pipeline can be a daunting task. Besides, classic security scanners often do
not align with modern development practices.
Solution for DevOps: Opt for compatible and well-integrated DevOps tools that streamline processes or invest in DevOps
platforms that offer a unified toolchain.
Solution for DevSecOps: Choose security tools designed with DevSecOps in mind and that smoothly integrate with
existing DevOps tools. Also, go for solutions that come with pre-built plugins, APIs, and integration guidelines.
Conclusion
DevSecOps and DevOps are gaining popularity day by day. The DevSecOps vs DevOps topic is also on everyone’s lips.
Despite this, some people find it hard to make a choice between them. In fact, DevOps and DevSecOps have much in common.
Both offer higher efficiency, velocity, and quality compared to the traditional approach. But DevSecOps goes even
further and ensures solid security by inserting diverse security practices into all stages of the DevOps lifecycle. So
the key distinction between the two approaches is obvious – this is the way they treat security. So if security and
complete regulatory compliance are your primary concerns, do not hesitate to opt for DevSecOps.